AI-Generated post 10 min to read
Unified, Automated, Secure: The New Paradigm of Multi-Tenant Organizations.
Balancing Efficiency and Security in Multi-Tenant Collaborations.
Interconnectivity Multi-Tenancy: Where Automation Meets Security Vigilance.
Multi-tenant Organization Templates in Microsoft 365
Azure Active Directory is undergoing a name change to Microsoft Entra ID. With this evolution, Microsoft is introducing the concept of multi-tenant organization templates. This feature is currently in preview, but it promises to bring a new level of organization and control for administrators managing multi-tenant collaborations.
Key Takeaways:
-
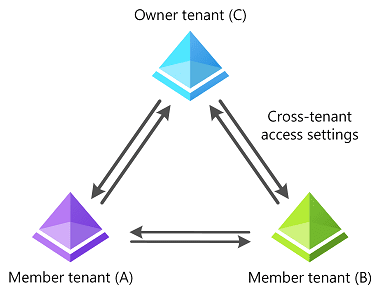
Guiding Principle for Collaboration: The essence of multi-tenant organization collaboration is to ensure administrators remain in control of their resources. For every tenant-to-tenant relationship, specific cross-tenant access settings are essential. These settings are explicitly configured by tenant administrators for identity synchronization and partner configurations within the multi-tenant organization.
-
Autogeneration of Cross-tenant Access Settings: In a multi-tenant organization, each tenant pair must have bi-directional cross-tenant access settings. These settings form the foundation for trust and sharing of users and applications. When a tenant joins a multi-tenant organization, if the required settings don’t already exist, they are autogenerated in an unconfigured state.
-
Policy Templates at Formation: To reduce the administrative workload during the formation of a multi-tenant organization, policy templates can be used. These templates preemptively configure cross-tenant access settings, ensuring that every partner tenant in the organization has the necessary settings in place.
-
Scoping and Additional Properties: Administrators have the flexibility to decide when cross-tenant access settings should be amended according to policy templates. They can choose to apply these settings to new partner tenants, existing partner tenants, or both.
-
Microsoft 365 Admin Center’s Use of Policy Templates: When forming a multi-tenant organization in the Microsoft 365 admin center, certain template settings are agreed upon. For instance, identity synchronization is set to allow user synchronization into the tenant, and cross-tenant access is configured to automatically redeem user invitations for both inbound and outbound.
Thought-Provoking Questions:
-
Future of Multi-tenancy: With Azure Active Directory transitioning to Microsoft Entra ID and the introduction of multi-tenant organization templates, how will the landscape of multi-tenancy evolve in the coming years?
-
Impact on Administrators: How will the introduction of policy templates and autogeneration of cross-tenant access settings streamline the administrative tasks associated with managing multi-tenant collaborations?
-
Security Implications: As multi-tenant organizations become more interconnected with the use of templates and automated settings, what are the potential security implications, and how can they be mitigated?
For a deeper dive into this topic and to understand the technical intricacies, you can refer to the official documentation.
The transition of Azure Active Directory to Microsoft Entra ID and the introduction of multi-tenant organization templates signal a significant shift in Microsoft’s approach to identity management and multi-tenancy. Here’s how the landscape of multi-tenancy might evolve in the coming years:
-
Unified Identity Management: With Microsoft Entra ID, we can expect a more unified and streamlined identity management system. This could mean better integration with other Microsoft services, leading to a more cohesive experience for both administrators and end-users.
-
Enhanced Collaboration: The introduction of multi-tenant organization templates is a clear indication of Microsoft’s focus on enhancing cross-organization collaboration. Organizations will find it easier to collaborate with partners, vendors, and other external entities, leading to more integrated business ecosystems.
-
Granular Control: The new features provide administrators with more granular control over cross-tenant access settings. This will allow organizations to fine-tune their collaboration settings, ensuring that they can maintain security while also facilitating seamless collaboration.
-
Security Enhancements: As multi-tenancy becomes more interconnected, there will be an increased focus on security. We can expect Microsoft to introduce more advanced security features, such as improved threat detection, enhanced logging, and better anomaly detection, to ensure that multi-tenant collaborations remain secure.
-
Simplified Administration: The use of templates and autogeneration of settings will simplify administrative tasks. This will reduce the overhead associated with managing multi-tenant collaborations, allowing IT teams to focus on more strategic initiatives.
-
Increased Adoption of Cloud Services: As multi-tenancy becomes more streamlined and secure, more organizations might be inclined to adopt cloud services. This could lead to an increase in the adoption of other Azure services, further solidifying Microsoft’s position in the cloud market.
-
Customization and Flexibility: With policy templates and other advanced features, organizations will have the flexibility to customize their multi-tenant settings to suit their specific needs. This will allow for more tailored collaborations, catering to the unique requirements of different industries and sectors.
-
Evolution of Compliance and Governance: As multi-tenancy evolves, there will be a need for updated compliance and governance policies. Microsoft, along with other industry players, might introduce new standards and best practices to ensure that multi-tenant collaborations remain compliant with global regulations.
In conclusion, the transition to Microsoft Entra ID and the introduction of multi-tenant organization templates are just the beginning of a new era in multi-tenancy. We can expect significant advancements in this space, with a focus on enhanced collaboration, security, and administrative efficiency.
The introduction of policy templates and autogeneration of cross-tenant access settings in the context of multi-tenant collaborations brings about a transformative change in administrative workflows. Here’s how these features will streamline administrative tasks:
-
Standardization: Policy templates allow for the creation of standardized settings across multiple tenants. This means that administrators can define a set of preferred settings once and apply them across various collaborations, ensuring consistency and reducing the chances of configuration errors.
-
Efficiency in Onboarding: The autogeneration of cross-tenant access settings accelerates the process of onboarding new tenants or partners. Instead of manually configuring settings for each new tenant, the system can automatically apply predefined settings, significantly reducing the time and effort required.
-
Reduced Complexity: Managing multi-tenant collaborations can be complex, especially when dealing with multiple partners, each with its own set of requirements. Policy templates simplify this by providing a framework that can be easily replicated across different tenants, ensuring that all partners adhere to a common set of guidelines.
-
Enhanced Security: By using standardized templates, organizations can ensure that security best practices are consistently applied across all tenants. This reduces the risk of security oversights that can occur when configurations are done manually for each tenant.
-
Flexibility and Customization: While templates provide a standardized approach, they also offer flexibility. Administrators can customize templates based on specific collaboration needs, ensuring that each tenant-to-tenant relationship is tailored to its unique requirements.
-
Proactive Management: The autogeneration feature ensures that as new tenants join a multi-tenant organization, the necessary cross-tenant access settings are automatically created. This proactive approach ensures that there are no gaps in configuration, leading to smoother collaborations.
-
Reduced Administrative Overhead: With templates and autogeneration, the need for repetitive tasks is minimized. Administrators no longer need to go through the same configuration steps for each tenant, freeing up their time for other critical tasks.
-
Consistent Policy Enforcement: Policy templates ensure that all tenants in a multi-tenant collaboration adhere to the same set of policies. This consistency is crucial for regulatory compliance and ensures that all partners in the collaboration are on the same page.
-
Ease of Updates: If there’s a need to update a particular setting across multiple tenants, administrators can modify the policy template, and the changes can be propagated to all associated tenants. This centralized approach to updates ensures consistency and reduces the chances of oversight.
-
Clarity and Transparency: With standardized templates, it becomes easier for administrators to communicate and explain the collaboration settings to stakeholders. This transparency builds trust and ensures that all parties involved understand the collaboration’s parameters.
In summary, the introduction of policy templates and autogeneration of cross-tenant access settings represents a paradigm shift in managing multi-tenant collaborations. These features not only simplify administrative tasks but also ensure consistency, security, and efficiency across the board.
The increased interconnectivity in multi-tenant organizations, facilitated by templates and automated settings, undoubtedly brings about numerous advantages in terms of efficiency and standardization. However, it also introduces potential security implications. Let’s delve into these implications and explore mitigation strategies:
- Uniform Vulnerability: Using standardized templates means that if there’s a vulnerability in the template, it could be exploited across all tenants using that template.
- Mitigation: Regularly review and update templates to ensure they adhere to the latest security best practices. Conduct periodic security audits of templates to identify and rectify potential vulnerabilities.
- Over-Privileged Access: Automated settings might inadvertently grant excessive permissions, leading to potential unauthorized access.
- Mitigation: Implement the principle of least privilege (PoLP) when designing templates. Regularly review and audit permissions to ensure they are appropriately assigned.
- Lack of Individual Customization: While templates provide standardization, they might not cater to the specific security needs of individual tenants.
- Mitigation: Allow for template customization where necessary, ensuring that individual tenants can tweak settings to fit their unique security requirements.
- Potential for Misconfiguration: The ease of deploying templates might lead to them being applied without thorough scrutiny, leading to potential misconfigurations.
- Mitigation: Implement a robust change management process. Ensure that any application of a template or change in settings undergoes a review and approval process.
- Reduced Visibility: With automation, there’s a risk that administrators might not be fully aware of all the settings applied, leading to potential oversight.
- Mitigation: Provide comprehensive logging and reporting tools. Ensure that administrators receive notifications of significant changes and have a dashboard to review current configurations.
- Dependency Risks: If a central template or setting is compromised, it could have cascading effects on all interconnected tenants.
- Mitigation: Implement robust monitoring and anomaly detection tools. Ensure rapid response capabilities to address any detected anomalies or breaches.
- Data Spillover Risks: Increased interconnectivity might lead to unintended data sharing or spillover between tenants.
- Mitigation: Clearly define data boundaries and implement data loss prevention (DLP) tools. Regularly audit data flows between tenants to detect and address any anomalies.
- Reduced Isolation: Multi-tenancy inherently involves shared resources. Increased interconnectivity might reduce the isolation between tenants.
- Mitigation: Implement strong segmentation and isolation practices. Use virtualization and containerization to ensure that tenants’ operations don’t overlap or interfere with each other.
- Phishing and Social Engineering: Attackers might exploit the trust established between interconnected tenants.
- Mitigation: Implement strong authentication mechanisms, including multi-factor authentication (MFA). Regularly train users about the risks of phishing and how to recognize potential threats.
- Template Tampering: Malicious actors might attempt to tamper with templates to introduce vulnerabilities.
- Mitigation: Store templates in a secure environment with strict access controls. Implement integrity checks to ensure templates haven’t been tampered with before deployment.
In conclusion, while the increased interconnectivity in multi-tenant organizations offers numerous benefits, it also introduces potential security challenges. By being proactive and implementing robust security practices, organizations can mitigate these risks and ensure a secure multi-tenant environment.
Further readings
- Set up a multi-tenant org in Microsoft 365 (Preview)
- Multi-tenant organization templates (Preview)
- Topologies for cross-tenant synchronization
- Enhance Your Online Security: A Step-by-Step Guide to Implementing Two-Factor Authentication (2FA)
If you are interested in Citizen Development, refer to this book outline here on Empower Innovation: A Guide to Citizen Development in Microsoft 365
| Now, available on | ||||
|---|---|---|---|---|
|
|
||||

|
||||
|
|
|
|
|
|
If you wish to delve into GenAI, read Enter the world of Generative AI
Also, you can look at this blog post series from various sources.
Stay tuned! on Generative AI Blog Series
We are advocating citizen development everywhere and empowering business users (budding citizen developers) to build their own solutions without software development experience, dogfooding cutting-edge technology, experimenting, crawling, falling, failing, restarting, learning, mastering, sharing, and becoming self-sufficient.
Please feel free to Book Time @ topmate! with our experts to get help with your Citizen Development adoption.
Certain part of this post was generated through web-scraping techniques using tools like Scrapy and Beautiful Soup. The content was then processed, summarized, and enhanced using the OpenAI API and WebPilot tool. We ensure that all content undergoes a thorough review for accuracy and correctness before publication



Comments